Top 10 AI Marketing Apps & Benefits – Power of Artificial Intelligence
2 years agoBeware! FACEBOOK HACKED – Types of Scams & How to Protect
2 years ago -
In the age of the digital world, social media platforms have become an integral part of our human lives. Facebook, with its billions of users, is one of the most popular social networking sites worldwide. Why is it that almost everyone seems to know someone who has fallen victim to a Facebook hack? This article delves into the reasons behind the prevalence of Facebook hacking and explores ways to safeguard your account.
Table of Contents
Understanding the Motivation Behind Facebook Hacking
Before we dive into the how-tos of protecting your Facebook account, let’s first understand why hackers are so drawn to it. There are various motivations behind these attacks, ranging from stealing personal information for financial gain to malicious intent like spreading misinformation or tarnishing one’s online image.
Common Methods of Facebook Hacking
The question of whether everyone gets their Facebook hacked is a complex one. In today’s digital age, cybersecurity threats are prevalent, and many individuals and organizations face the risk of being hacked. Cybercriminals use a variety of tactics, such as malware, phishing, ransomware, and social engineering, to target individuals and organizations. As a result, many people have experienced some form of hacking or cyber-attack, either directly or indirectly.
Hacking involves the use of technology or technical expertise to address and overcome various challenges or obstacles. Hackers can fall into two categories: those with altruistic motives, such as the ethical hackers we collaborate with at Avast, or those with malicious intent, like the individuals who breached Facebook’s security in 2018. Regardless of their intentions, hacking demands an in-depth understanding of technology and a high level of programming skills.
In contrast, phishing represents a form of social engineering that manipulates individuals into willingly disclosing sensitive information. Phishing schemes can range from simplistic approaches, such as sending a message containing a deceptive link like “discover who passed away”, “Job vacancies offers”, to more intricate tactics, such as tech support scams. However, all phishing techniques rely on some form of electronic communication to deceive and defraud individuals.
FACEBOOK HACKED: Hacking Vs Phishing
| Aspect | Hacking | Phishing |
|---|---|---|
| Definition | It can encompass a wide range of activities, from exploiting software vulnerabilities to unauthorized access. | A deceptive attempt to acquire sensitive information, such as login credentials or financial details, by posing as a trustworthy entity. |
| Method | Utilizes technical skills to break into systems, exploit vulnerabilities, and gain unauthorized access. | Relies on social engineering techniques to trick individuals into revealing their information or clicking on malicious links. |
| Scope | Can encompass a wide range of activities, from exploiting software vulnerabilities to unauthorized access. | Primarily focused on tricking individuals through email, messages, or websites. |
| Goal | May seek to gain control, steal data, or compromise the integrity of a system or network. | Aims to deceive individuals into revealing personal or financial information. |
| Complexity | Generally requires technical expertise and knowledge of security systems. | Requires knowledge of psychology and social manipulation rather than technical expertise. |
| Targets | Targets can include individuals, organizations, or entire systems and networks. | Primarily targets individuals, often casting a wide net to reach a large audience. |
| Delivery Method | Attack vectors may include exploiting software vulnerabilities, using malware, or employing advanced technical methods. | Typically delivered through deceptive emails, fake websites, or fraudulent messages. |
| Legality | Hacking is illegal and considered a cybercrime in most jurisdictions. | Phishing is also illegal and falls under cybercrime laws in many countries. |
| Prevention | Security measures such as firewalls, intrusion detection systems, and strong access controls are used to prevent hacking. | Phishing awareness training, email filters, and user education are essential in preventing phishing attacks. |
| Examples | Examples of hacking include network intrusions, SQL injections, and exploiting software vulnerabilities. | Examples of phishing include deceptive emails from fake banks, social media login pages, or requests for personal information. |
Both hacking and phishing are cybersecurity threats, but they differ in their methods, goals, and the skills required to execute them. It’s important to be aware of these distinctions to better protect against these threats.
Phishing Attacks for Facebook Hacking
How Phishing Works
Phishing is one of the most common methods employed by hackers to gain unauthorized access to Facebook accounts. It involves creating fake login pages that mimic Facebook’s official page. Unsuspecting users enter their credentials, believing they are logging into their account, while in reality, they are handing over their details to cybercriminals.
Signs of a Phishing Attempt
- Suspicious or misspelled URLs.
- Urgent requests for personal information.
- Emails or messages from unknown sources asking for login details.
Weak Passwords
The Importance of Strong Passwords
Weak passwords are like an open invitation to hackers. Most users tend to use easily guessable passwords or fail to update them regularly. This practice makes it relatively simple for hackers to breach their accounts.
Common Password Mistakes
- Using easily guessable information like birthdates or names.
- Reusing passwords across multiple accounts.
- Ignoring the significance of changing passwords periodically.
Malware and Social Engineering
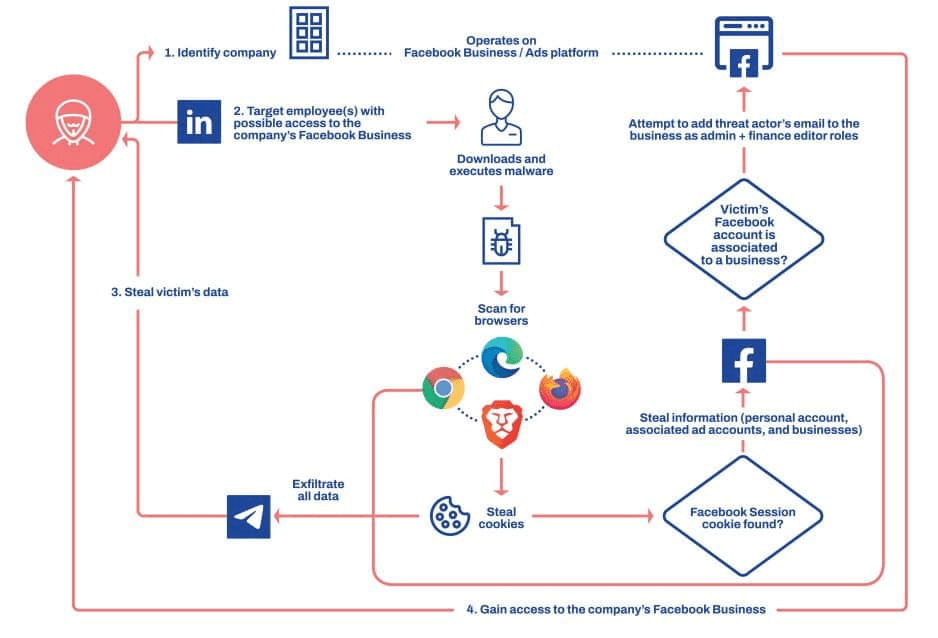
Malware’s Role in Facebook Hacking
Malware, often unknowingly downloaded onto users’ devices, can be used to compromise Facebook accounts. Additionally, social engineering tactics are used to manipulate users into revealing sensitive information or clicking on malicious links.
The Psychology of Social Engineering
Social engineering exploits human psychology to gain access to personal information. Hackers often pretend to be trustworthy individuals or organizations to manipulate users emotionally and psychologically, leading them to make errors that compromise their security.
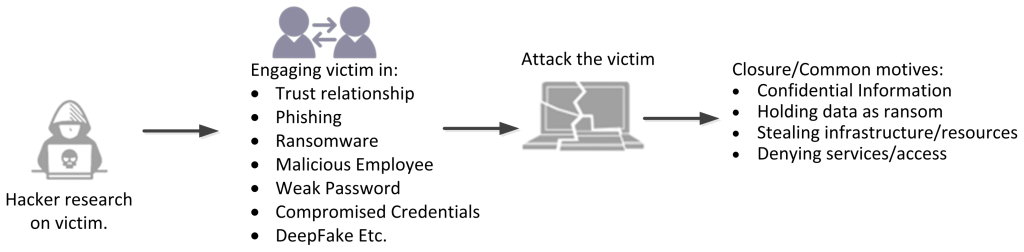
Types of Scams for Facebook Hacking
There are several types of Facebook scams that cybercriminals use as tactics to hack accounts or gain unauthorized access. Here are some common methods they apply to Facebook scams:
Phishing Scams
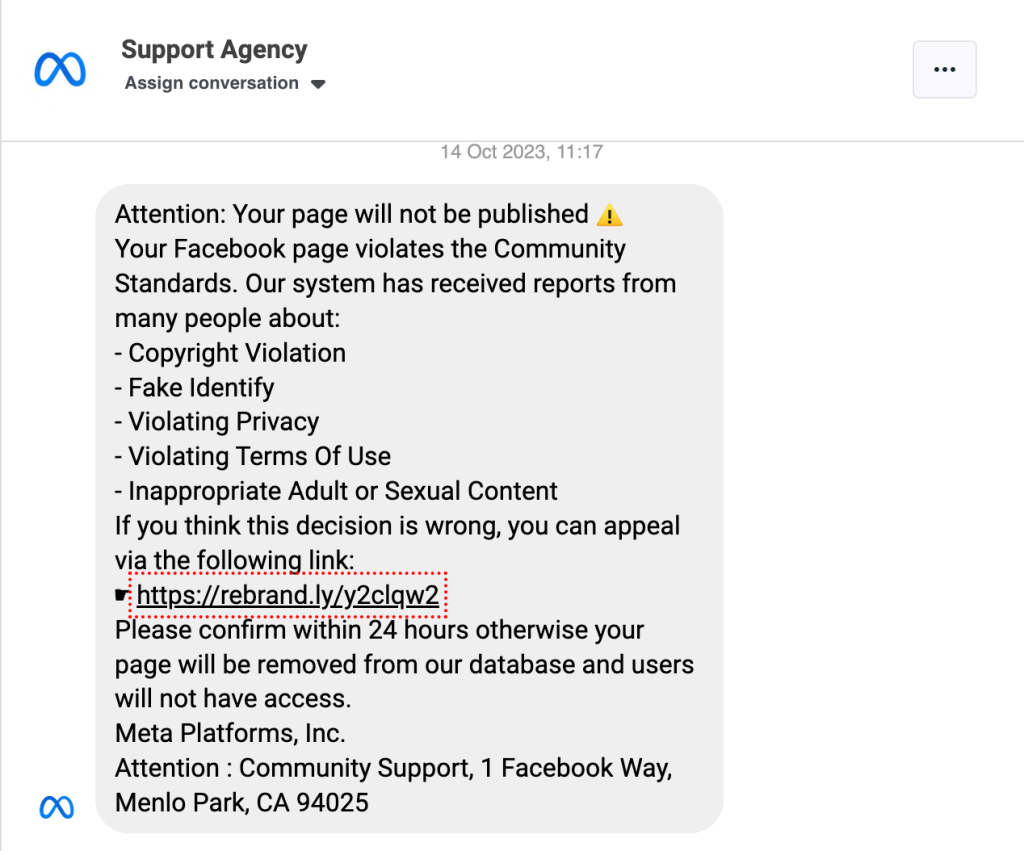
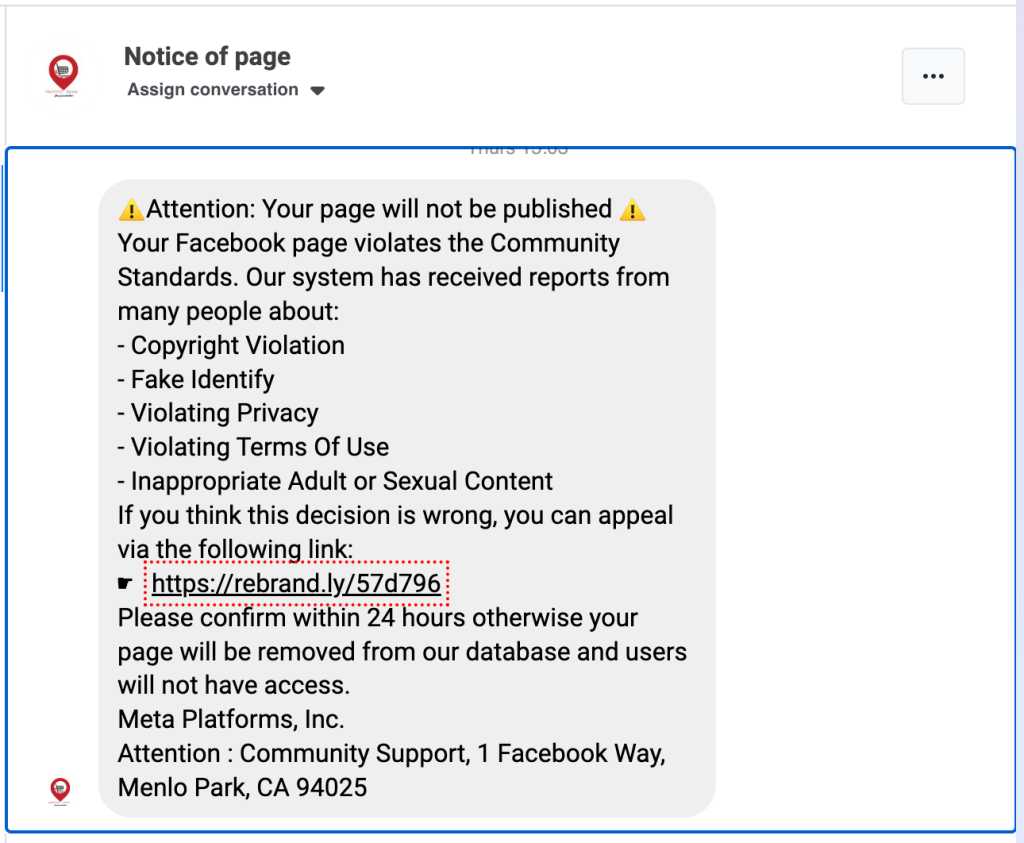
Phishing is a prevalent method where scammers create fake login pages that mimic Facebook’s official login page. They send deceptive messages, emails, or posts with links to these fake pages. Once users enter their login information, the scammers gain access to their Facebook accounts.
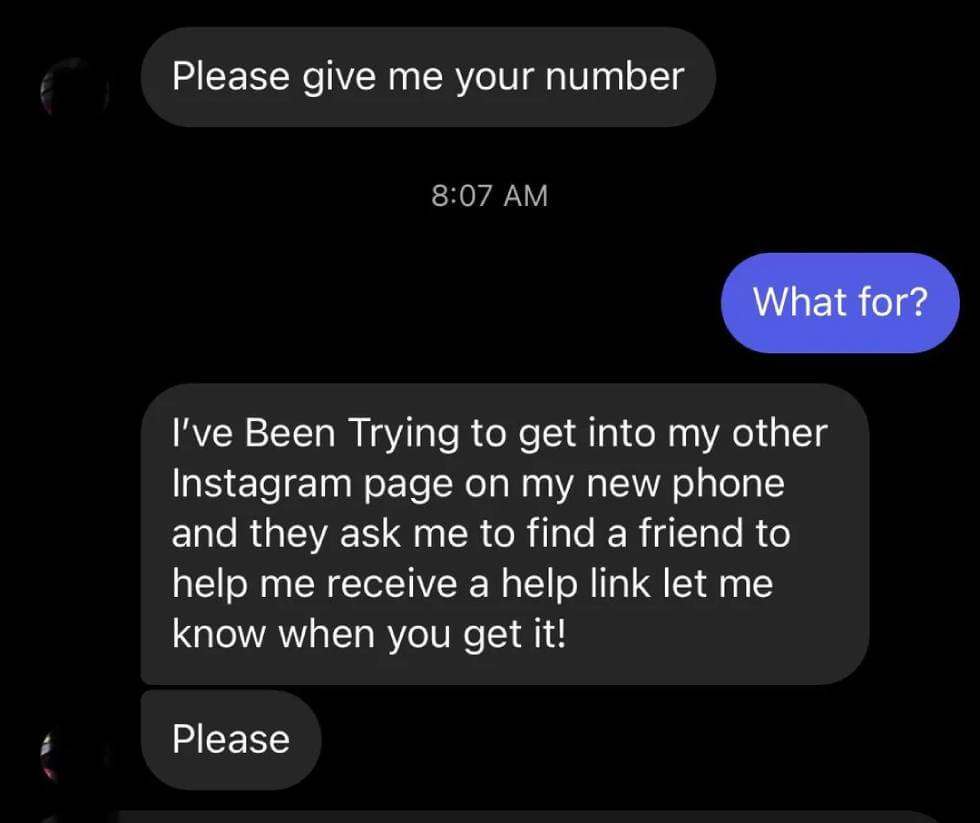
The following examples are from Facebook Messenger, which I recently got on my couple of my client pages.
Scams via Direct Messages Direct message (DM)
Scams serve as a channel for various social media phishing scams. In these instances, scammers send direct messages from the account of someone known to the victim, often containing baiting messages like “Is this a picture of you?” or “See who passed away,” accompanied by a link. This link directs the victim to a fraudulent login page with the intent to steal their login details or request payment to access the mentioned image or video.
These scammers exploit people’s trust in their social media acquaintances and their natural curiosity, coaxing victims into clicking without much thought and ultimately surrendering private information.
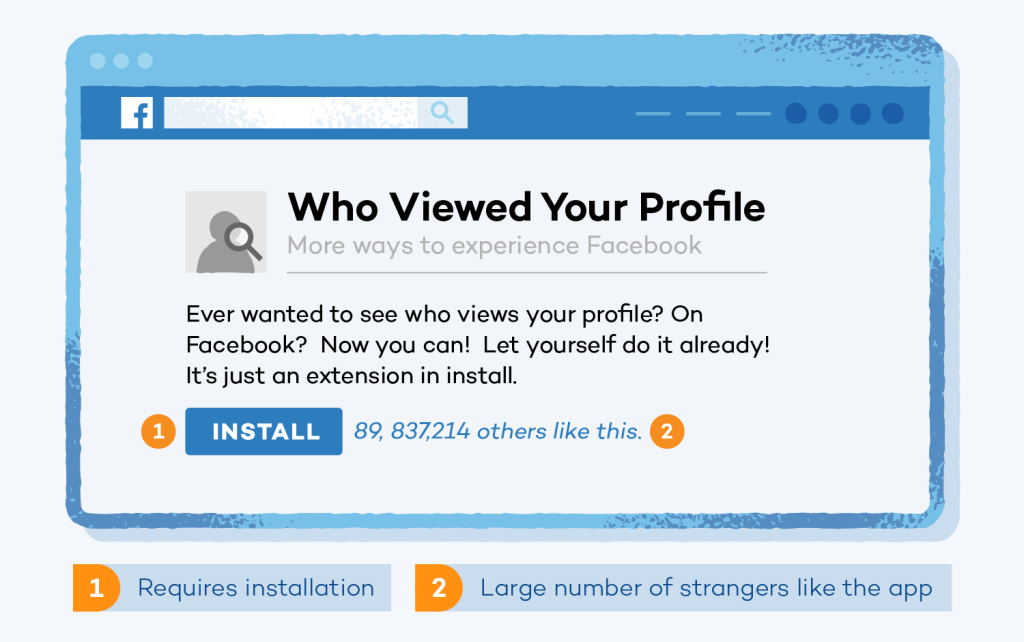
‘Who viewed my profile?’ scams
Have you ever come across an advertisement claiming to disclose your profile viewers? Avoid clicking on such ads. These advertisements are a type of phishing scheme exploiting human curiosity and self-interest. Their sole aim is to pilfer your social media login information, with the intent of either
a) infiltrating your accounts or
b) selling them on the dark web.
419 Scams
In these scams, fraudsters pose as friends or family members and claim to be in urgent need of money. They use hacked accounts to send messages asking for financial assistance. The scammers take advantage of the victim’s trust and emotions.
Malware and Viruses
Scammers may send links or attachments containing malware or viruses. Clicking on these links or downloading the files can compromise the security of a user’s device, potentially leading to unauthorized access or data theft.
Impersonation Scams
Hackers impersonate friends, family members, or celebrities and ask for money, claiming to be in dire situations. These scams exploit personal relationships to manipulate victims into sending money.
Ad Scams
Fraudulent advertisements can lead you to malicious websites or solicit payment for non-existent products.
Clickbait
Clickbait is designed to entice you with intriguing headlines that lead to irrelevant or harmful content.
Fake Contests and Giveaways
Cybercriminals create fake contests or giveaways, asking users to provide personal information, like email addresses and phone numbers, in exchange for the chance to win prizes. The collected data is then used for various fraudulent activities.
Phony Job Offers
One of the most common forms of job scams involves fraudulent job offers. Scammers pose as legitimate employers, posting enticing job openings that seem too good to be true. They often require personal information or an upfront payment for a job that doesn’t exist. Hackers are also Using Fake Job Ads to Steal People’s Identities is also increasing in recent days.
Tech Support Scams
Impersonating Facebook tech support representatives, scammers claim that the user’s account has issues and request remote access to the user’s device. This can lead to data theft or financial fraud.
Survey Scams
Users are enticed to participate in surveys that promise rewards or prizes. However, these surveys are often a ruse to gather personal information that can be used for identity theft or spam.
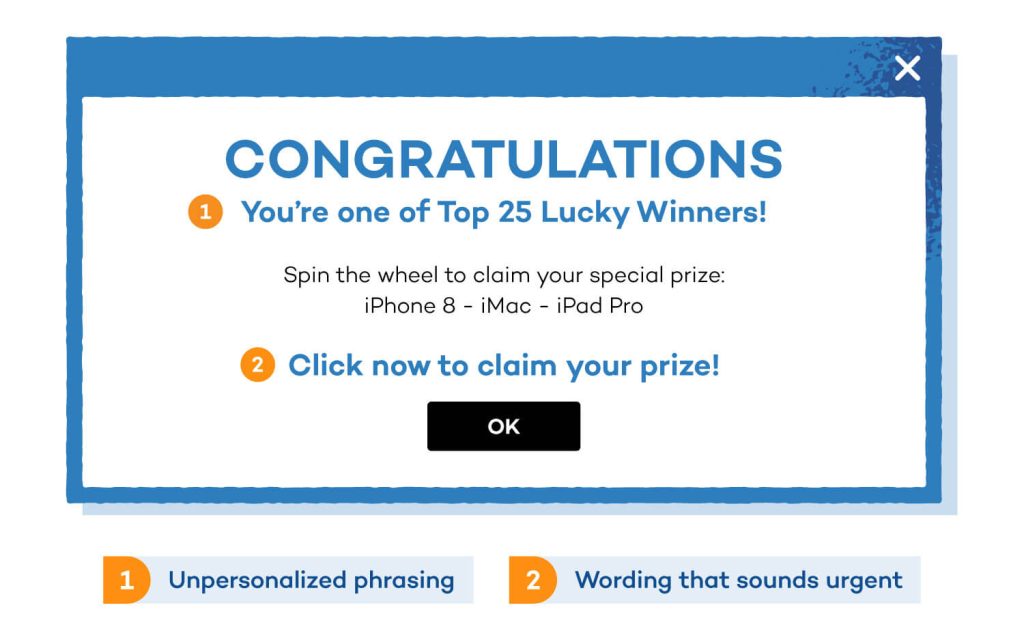
Lottery Scams
Users receive messages claiming they’ve won a Facebook lottery or prize. To claim the prize, they are asked to pay a fee or provide personal information, leading to financial loss and identity theft.
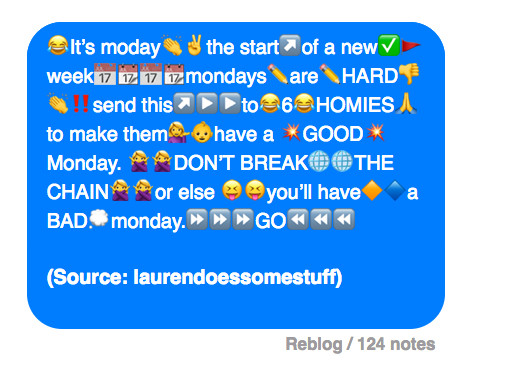
Chain letters
Chain letters manipulate users into sharing messages or information with the promise of good luck or fortune. For example: Forward this message or you will die in 10 days, send this message to 5 more friends and achieve good luck, etc.
It’s crucial for Facebook users to be vigilant and distrustful when encountering suspicious messages or requests. Using strong, unique passwords, enabling two-factor authentication, and regularly reviewing your account for any unauthorized activity are essential steps to protect your account. If you come across any suspected scams on Facebook, report them to the platform and educate yourself and your connections about online safety to reduce the risk of falling victim to these scams.
How to Protect Your Facebook Account from Facebook Hacking?
In an era where our digital lives are as important as our physical ones, safeguarding your Facebook account from hackers is paramount. Understanding the reasons behind the increasing number of Facebook hacks allows you to take proactive steps to protect your digital presence.
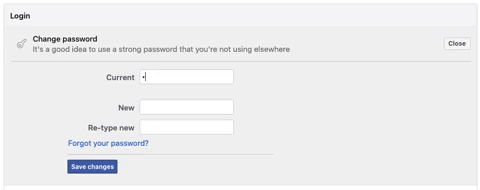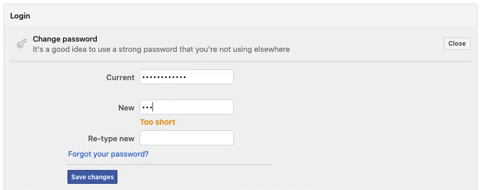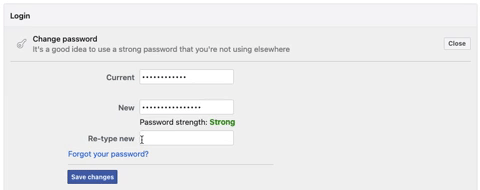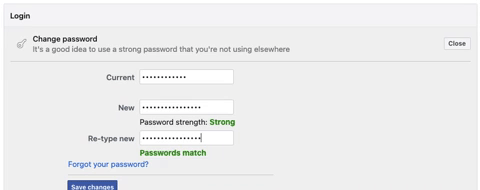
Strong Passwords
Create complex, unique passwords for your Facebook account and change them regularly. In the realm of cybersecurity, a strong password is your first line of defense against unauthorized access and security breaches. Given the increasing number of Facebook hacking in 2025, understanding the importance of a robust password is critical.
To create and maintain strong passwords for your Facebook account, consider the following best practices:
- Complexity: Use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid easily guessable sequences like “12345” or “password.”
- Length: Opt for longer passwords, as they are generally more secure. A good rule of thumb is to have a password that’s at least 12 characters in length.
- Uniqueness: Never reuse passwords across different platforms or accounts. Each account should have its unique password.
- Avoid Common Words: Avoid using easily guessable words, phrases, or personal information, such as your name or birthdate.
- Passphrase: Consider using a passphrase from Facebook hacking, which is are longer combination of words or phrases. They can be both secure and easy to remember.
- Regular Updates: Change your password periodically to enhance security. Never use the same password for an extended period.

Two-Factor Authentication
Enable two-factor authentication to add an extra layer of security to your account. In the ever-evolving landscape of cybersecurity and the increasing number of Facebook hacks, two-factor authentication (2FA) plays a crucial role in safeguarding your online presence.
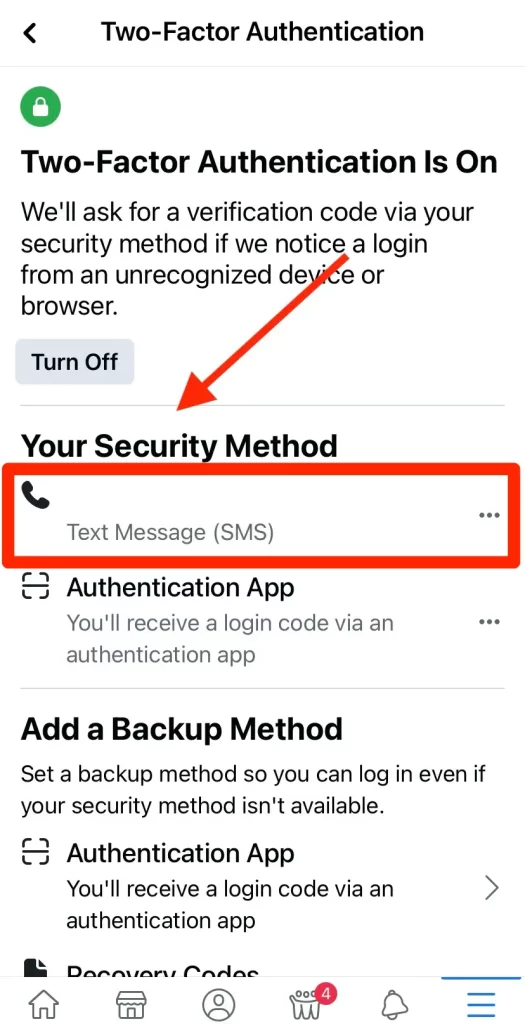
To enable and effectively use 2FA for your Facebook account, follow these steps:
- Go to Security Settings: Log in to your Facebook account, go to “Settings & Privacy,” and select “Settings.” Then, click on “Security and Login.” If you’re confused, then don’t worry, I’ll cover “How to Create a Facebook Page for Beginners? Hacks & Tricks to Grow your Business“
- Set Up 2FA: Under “Two-Factor Authentication,” click on “Use two-factor authentication.” Facebook offers multiple options for the second factor, such as authentication apps, text messages, or recovery codes.
- Choose Your Second Factor: Select the 2FA method that suits you best. An authentication app is a popular choice, as it generates temporary codes that change regularly.
- Follow the Setup Process: Depending on your chosen method, follow the setup process. For instance, if you opt for an authentication app, you’ll need to scan a QR code provided by Facebook and enter the generated code to complete the setup.
- Store Backup Codes: Facebook usually provides backup codes for emergency access. Store these codes securely in case you lose access to your second factor.
Beware of Clicking on Random Links
Particularly if they appear unusual! Consider whether your friend would genuinely send a link related to this topic. Furthermore, if they were to send a link, would it typically be a shortened one? Scammers often employ link shorteners to obscure the true destination of the link. Therefore, if the link appears suspicious, it’s likely a phishing attempt for Facebook Hacking.
Regular Security Updates
Stay updated with the latest security patches and updates for both the Facebook app and your browser.
To keep your account secure from Facebook hacking through regular security updates, consider these steps:
- Automatic Updates: Enable automatic updates for your operating system, web browser, and the Facebook app. This ensures that you receive the latest security patches promptly.
- Frequent Checks: Periodically verify that your software is up to date. Manually trigger updates if necessary, especially for your operating system and browser.
- Use Supported Software: If your operating system or browser is no longer supported by the manufacturer, consider upgrading to a newer version to continue receiving security updates.
- Beware of Phishing: Be cautious of phishing attacks, especially if you’re unable to update your software. Exercise heightened vigilance to avoid falling victim to such attacks.
- Security Software: Install and maintain reputable security software on your devices. These programs can help detect and block potential threats, even if your software is outdated.
Educate Yourself and Stay Informed
Cybersecurity threats are ever-evolving. It’s imperative to stay informed about the latest trends and tactics used by cybercriminals. Follow reputable cybersecurity blogs and news sources to keep yourself updated on potential risks.
Conclusion
In an era where our digital lives are as important as our physical ones, safeguarding your Facebook account from hackers is paramount. Understanding the reasons behind the increasing number of Facebook hacking incidents recently allows you to take proactive steps to protect your digital presence.
To conclude, it’s crucial to stay vigilant, adopt best practices in password management, and keep your security settings up to date. By doing so, you can reduce the risk of falling victim to the growing menace of Facebook hacks.
FAQs of Facebook Hacking
How can I create a strong password to secure my Facebook account?
Creating a strong password involves using a combination of letters, numbers, and special characters. Avoid using easily guessable information like your name or birthdate.
What is two-factor authentication, and why is it important for my Facebook account?
Two-factor authentication adds an extra layer of security by requiring you to provide a second form of verification, usually sent to your mobile device, in addition to your password. This makes it significantly harder for hackers to access your account.
How can I recognize a phishing attempt on Facebook?
Be cautious of unsolicited messages or requests for personal information. Double-check the sender’s identity and the website’s URL before sharing any details.
Are there tools or services that can help me manage and secure my online passwords?
Yes, password management tools can help you generate strong, unique passwords and store them securely. They can also assist in auto-filling login information.
What should I do if I suspect that my Facebook account has been hacked?
If you suspect your account has been compromised, change your password immediately, review your account activity, and report any suspicious activity to Facebook for further assistance.
What are some signs of a phishing attempt on Facebook hacked?
Signs of a Facebook hacking attempt on Facebook include suspicious or misspelled URLs, urgent requests for personal information, and emails or messages from unknown sources asking for login details.
Why is Two-Factor Authentication (2FA) important for Facebook security?
Two-factor authentication adds an extra layer of security to your Facebook account. Even if a hacker acquires your password, they won’t be able to access your account without the second authentication factor, typically a code sent to your mobile device.
Latest Articles:
- How to Optimize for Zero-Click Searches? Is It Bad for SEO?
- Metaverse Marketing: Social Media Marketing in the Metaverse
- What is On Page Optimization? Keyword, URL, Meta Tags, ALT Tags & MORE!
- AI vs Human Copywriting: 10 Reasons Why Human Copy is Better Than AI

![[2025 Updated] Top 10 Digital Marketing Agencies in Nepal Ranked!](https://mysticrubs.com/wp-content/uploads/2022/05/top-10-digital-marketing-company-in-nepal.png)